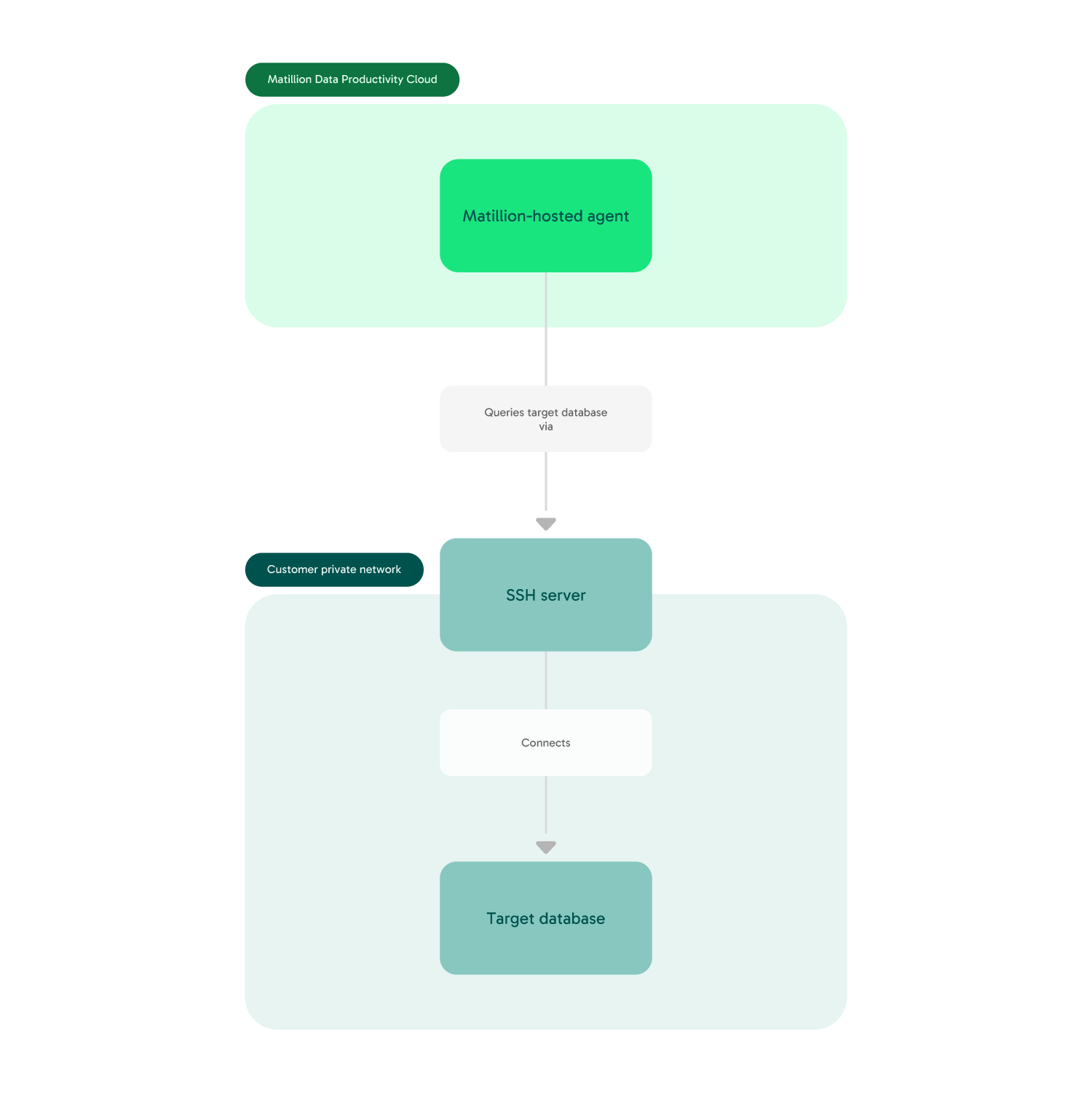
SSH Tunneling🔗
Matillion-hosted agents in the Data Productivity Cloud can connect to network-secured databases using an intermediate SSH server that is part of the same network as the target database.
Why use it?🔗
- Use Full SaaS Data Productivity Cloud without exposing your databases to the public Internet.
- Enables you to restrict database access to only those who can authenticate via SSH.
- Reduces the need for complex VPN setups by providing a straightforward way to secure connections to protected databases.
How to use it?🔗
This feature is available on a component-by-component basis. Customers using a Full SaaS Data Productivity Cloud solution can use the Database Query and RDS Query components to access data sources within their infrastructure using a configured SSH tunnel. This is accessed via the Networks tab. Read Networks to get started.
Connection URL and SSH tunnel behavior🔗
The component's connection URL specifies the database endpoint that the agent connects to after establishing an SSH tunnel.
The specific parameter that defines where the SSH tunnel should connect varies by component. Refer to the relevant component documentation for details.
Example connection URL🔗
In this example, my.postgres is a database server that is only accessible through an SSH tunnel:
{
"connectionUrl": "jdbc:postgresql://my.postgres:5432/test?loggerLevel=OFF"
}
How it works🔗
- The component runs and automatically establishes an SSH tunnel.
- Local port forwarding is configured to route traffic through the tunnel to
my.postgres:5432. - The application then connects to the database using the provided
connectionUrl, ensuring secure access to the database.
This setup enables seamless database connections over an SSH-protected network.